Ingestible Sensors and Sensing Systems for Minimally Invasive Diagnosis and Monitoring: The Next Frontier in Minimally Invasive Screening | ACS Sensors
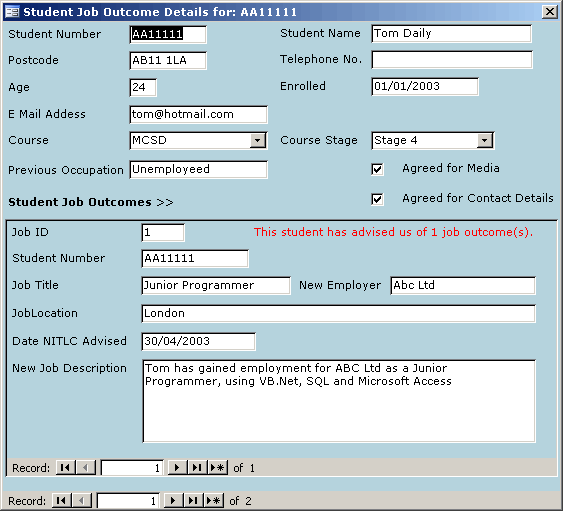
Prevent Duplicate Information from being entered into a Microsoft Access form | Database Solutions for Microsoft Access | databasedev.co.uk
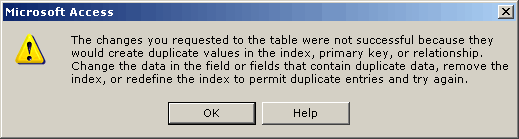






![Fix Access Denied Errors with Ease [CMD, Hard Drive, Folder] Fix Access Denied Errors with Ease [CMD, Hard Drive, Folder]](https://cdn.windowsreport.com/wp-content/uploads/2021/11/Access-is-denied-Windows-10-1200x900.jpg)