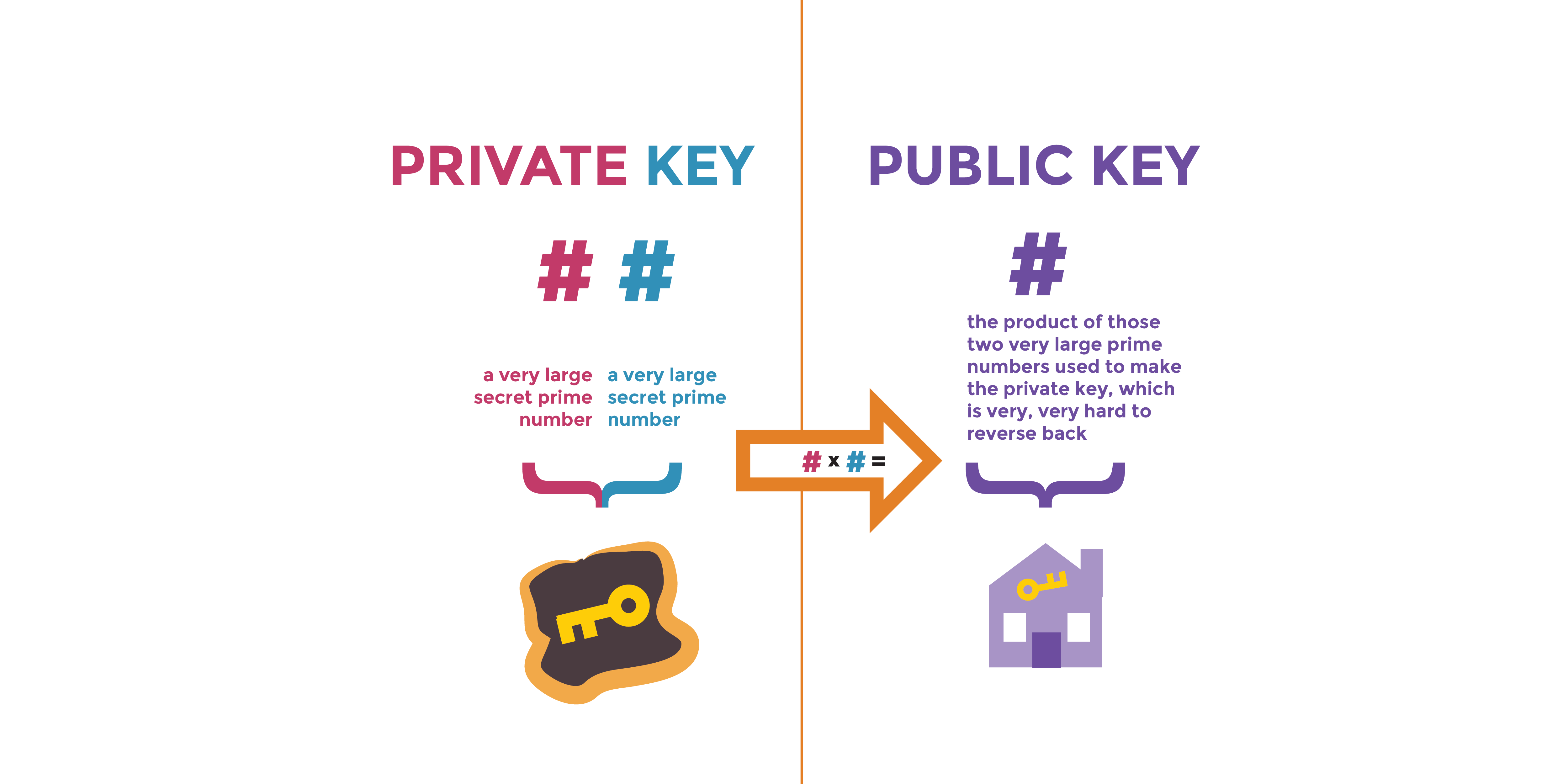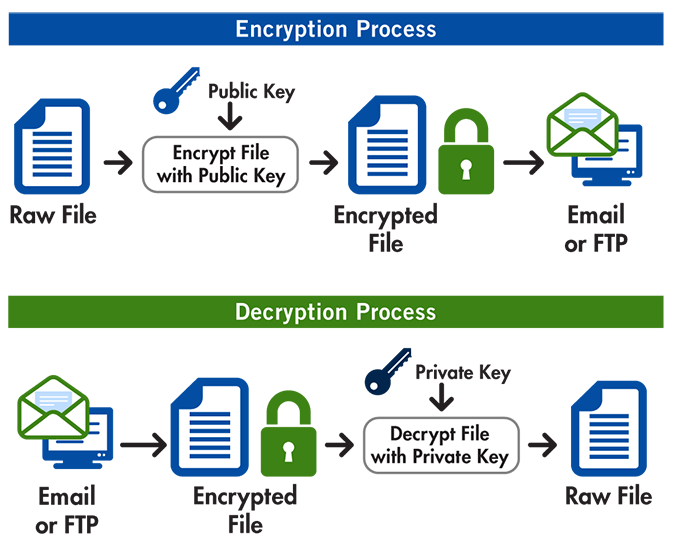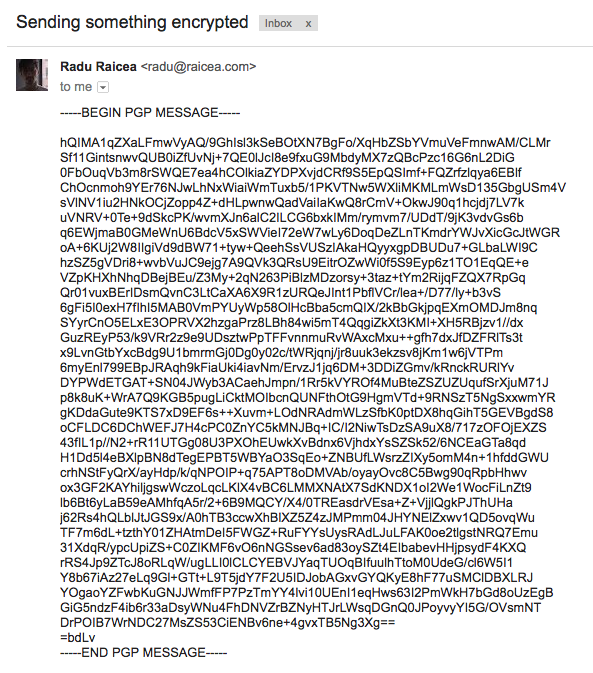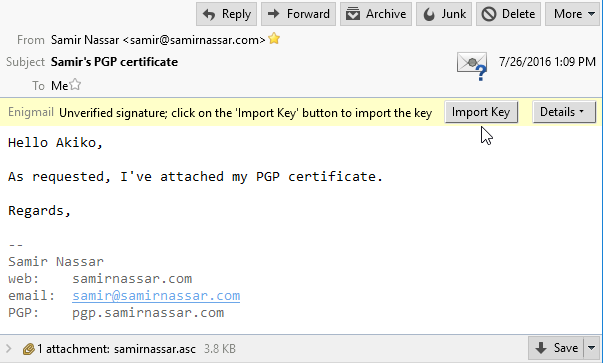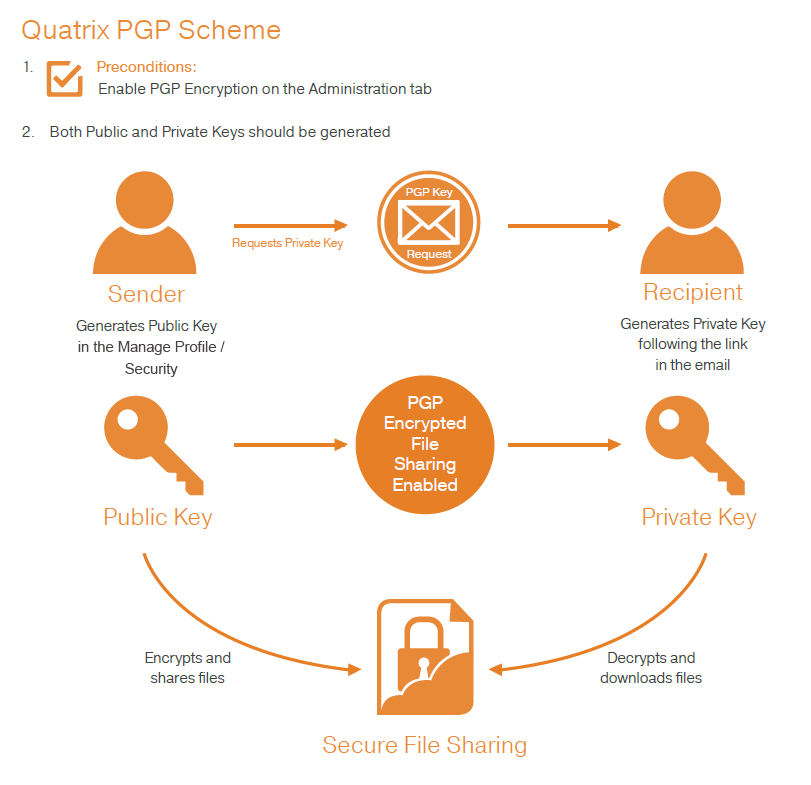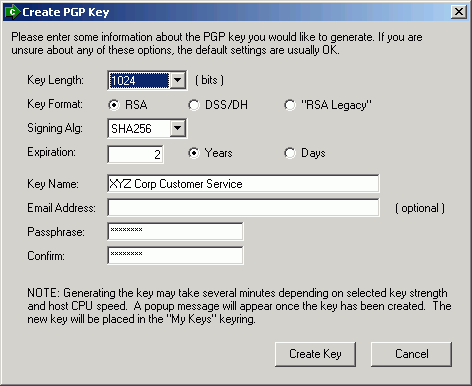
Using public-key crypto remains difficult – Networking notes – Recent articles, news and posts to help readers of the Computer Networking Principles, Protocols and Practice ebook to expand their networking knowledge

pgp - Why is GnuPG changing first two characters of ascii armored public key after downloading it from the key server? - Cryptography Stack Exchange