Researchers using Jupyter Notebooks or other S3-compatible data-science... | Download Scientific Diagram

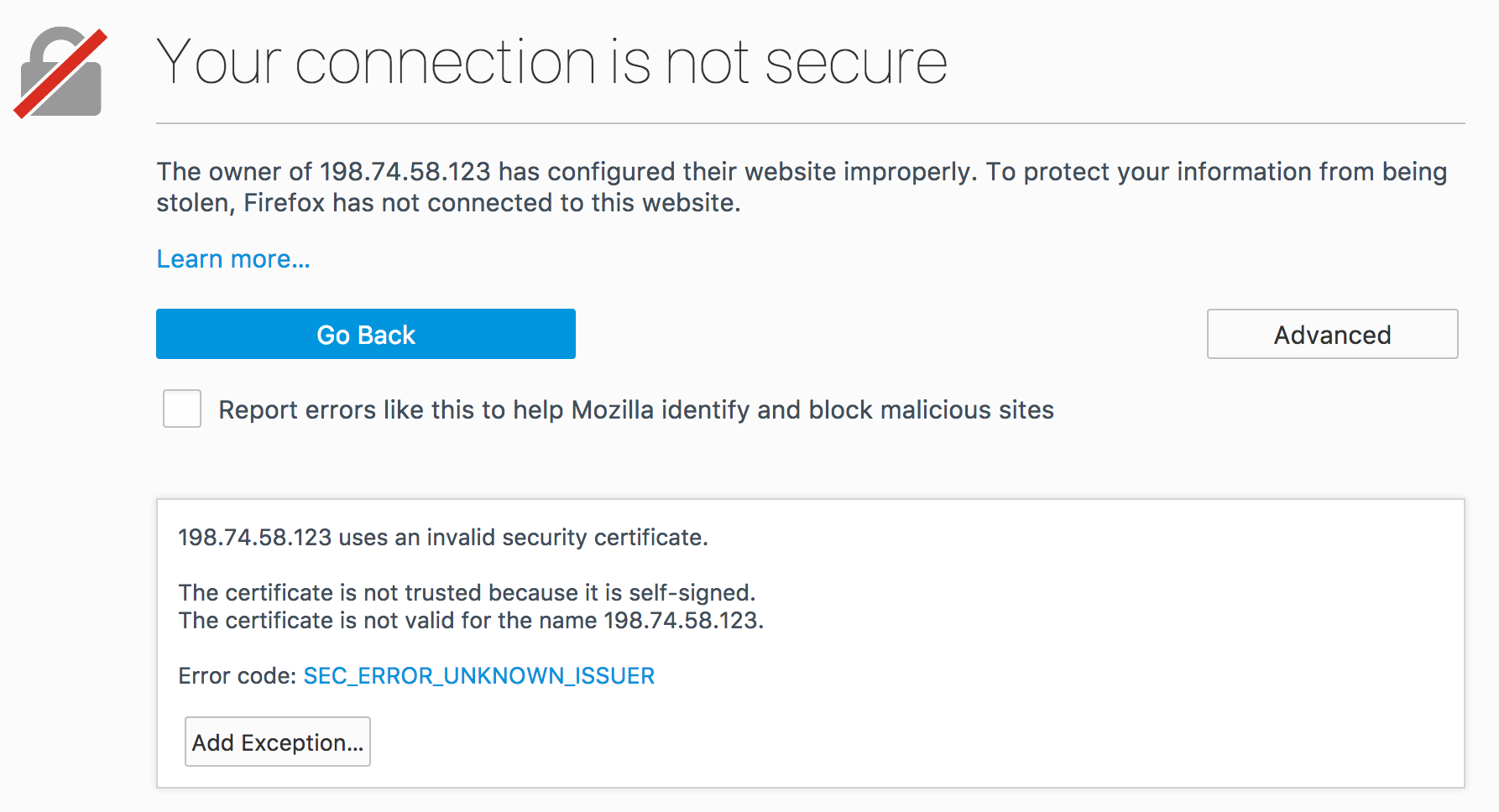
amazon web services - Cannot obtain a trusted connection when hosting Jupyter Notebook on AWS EC2 instance - Stack Overflow
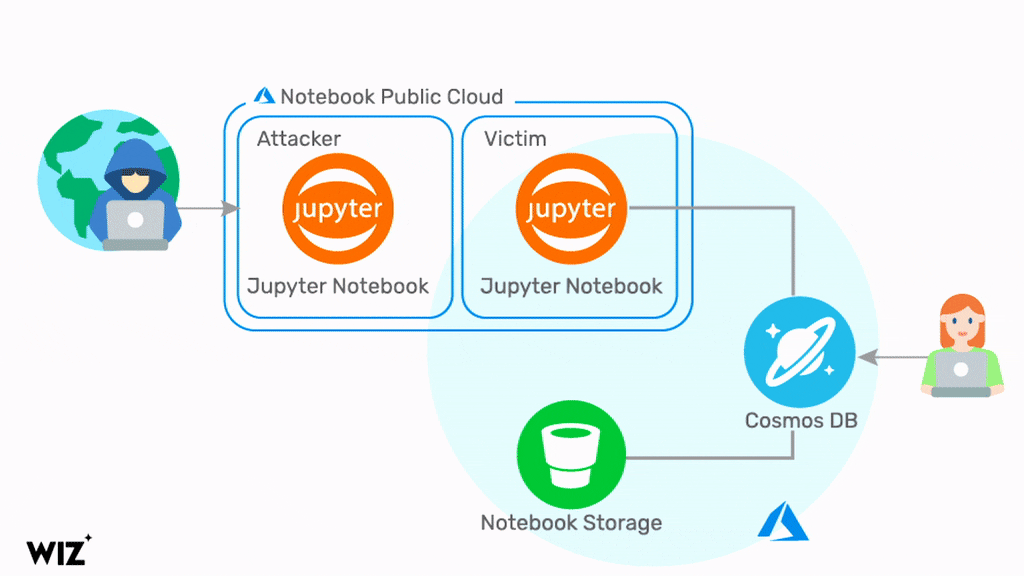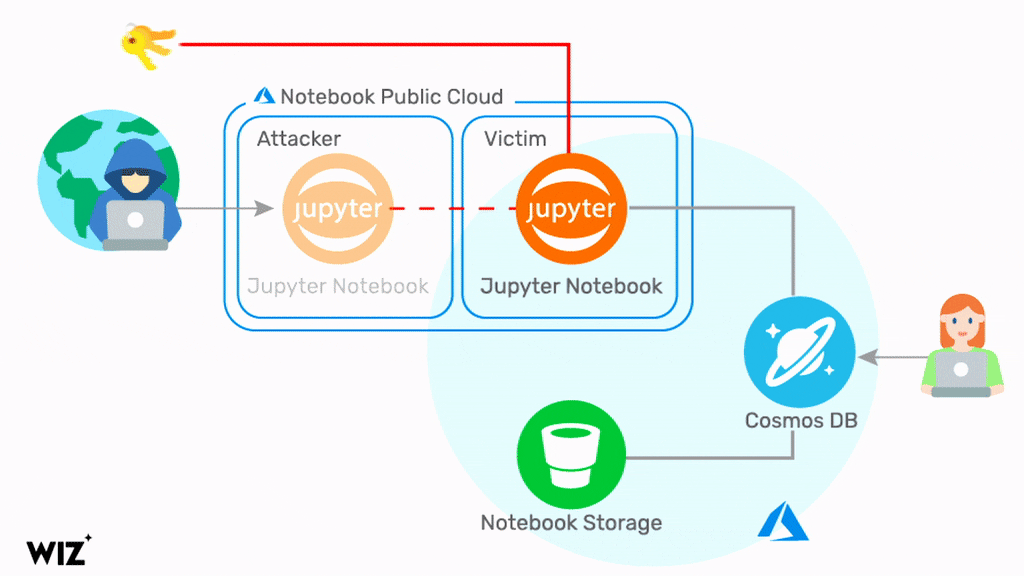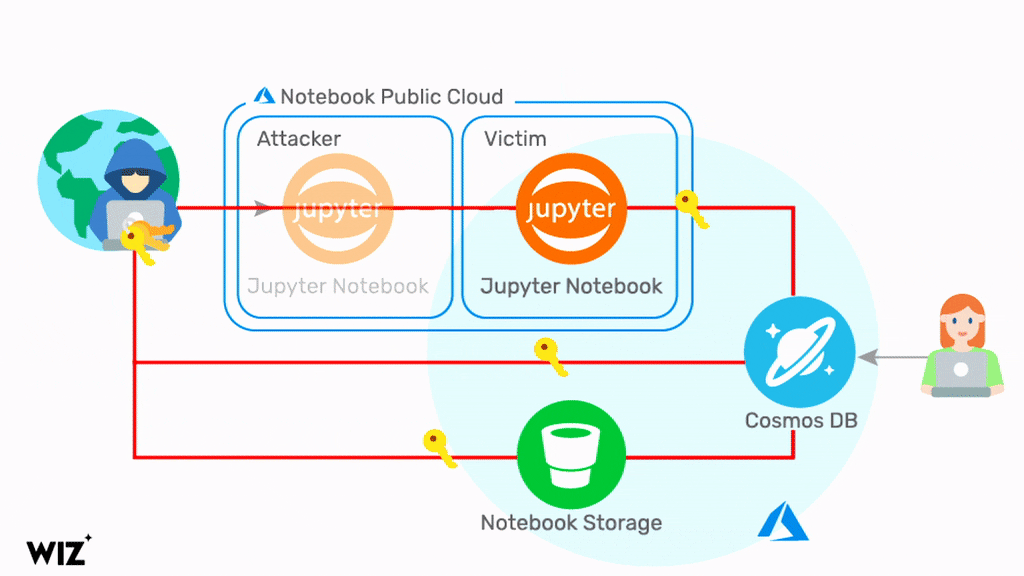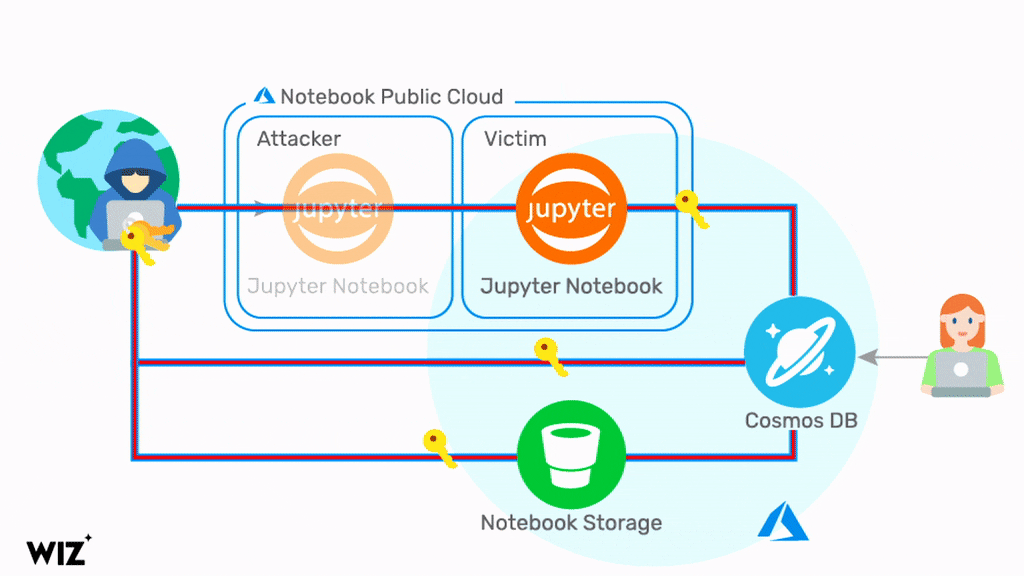
Microsoft Pulls Azure Cosmos DB Component After Major Security Issue Exposed - Petri IT Knowledgebase

Jupyter Notebook Manifesto: Best practices that can improve the life of any developer using Jupyter notebooks | Google Cloud Blog
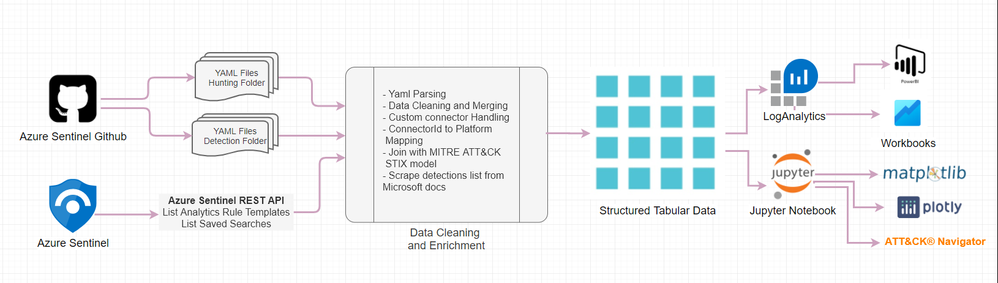
Using Jupyter Notebook to analyze and visualize Azure Sentinel Analytics and Hunting Queries - Microsoft Community Hub