MikroTik Firewall & NAT Bypass. Exploitation from WAN to LAN | by Jacob Baines | Tenable TechBlog | Medium

MikroTik Firewall & NAT Bypass. Exploitation from WAN to LAN | by Jacob Baines | Tenable TechBlog | Medium
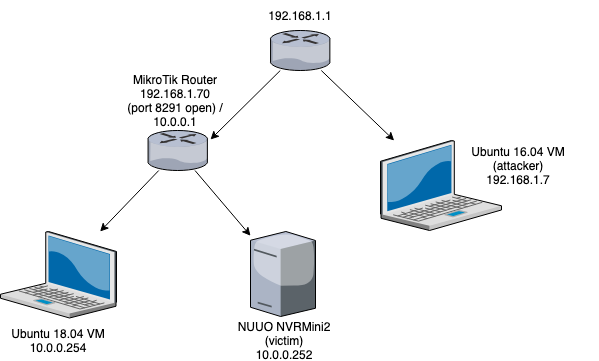
MikroTik Firewall & NAT Bypass. Exploitation from WAN to LAN | by Jacob Baines | Tenable TechBlog | Medium


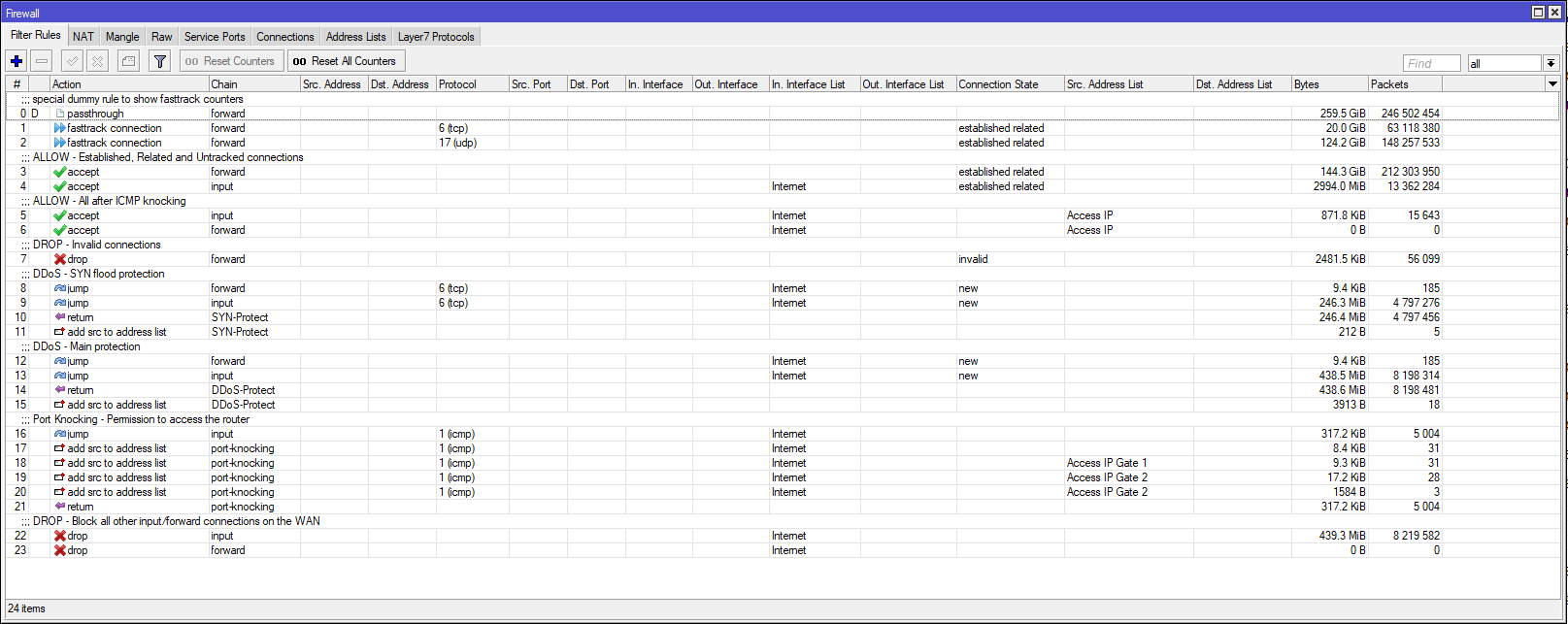

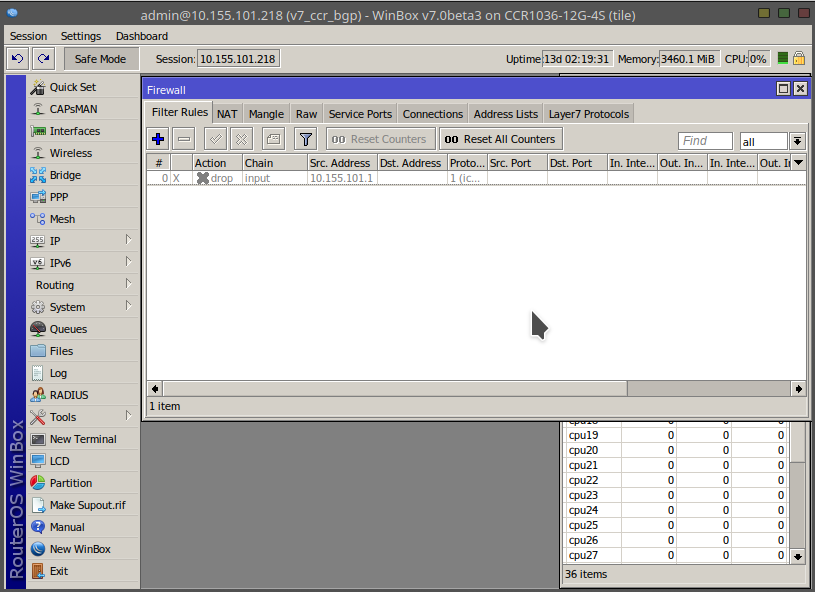
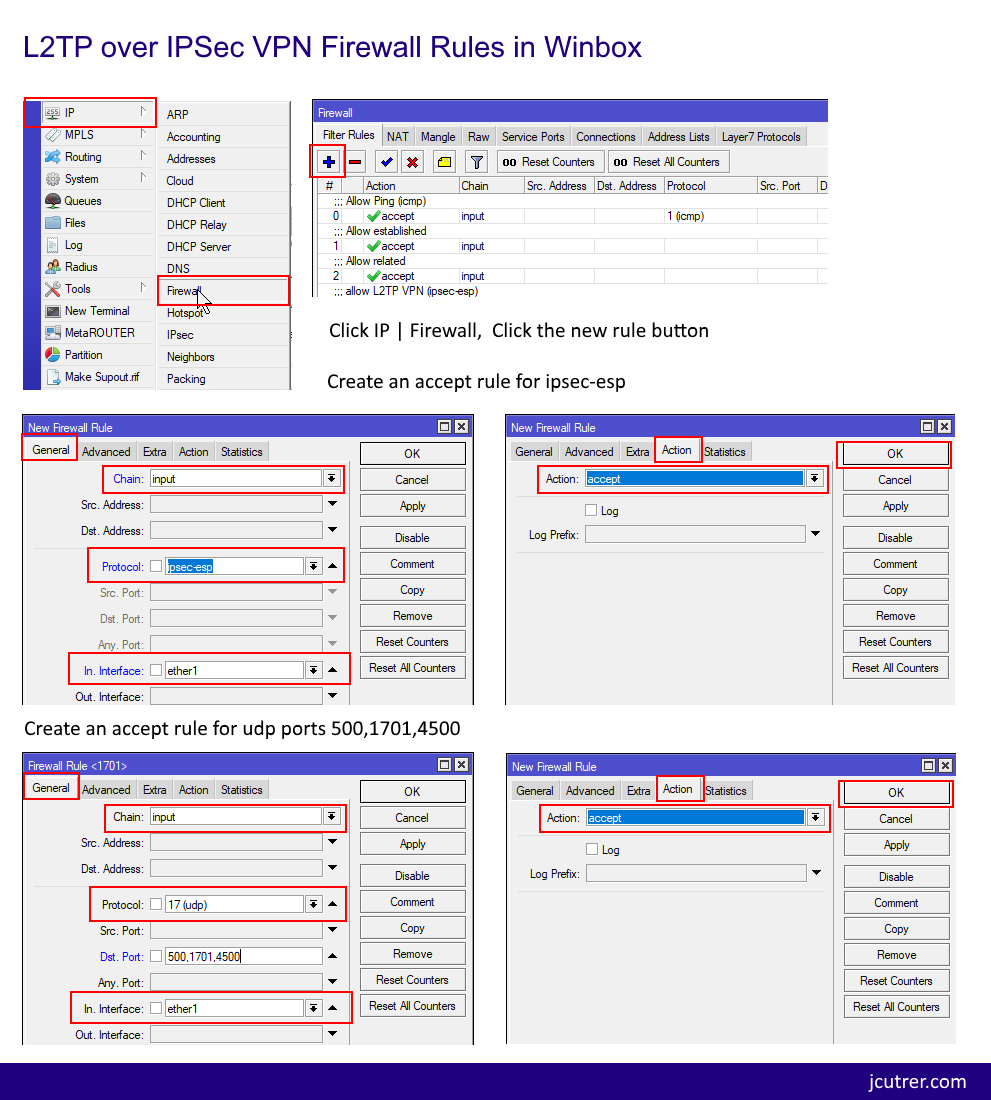





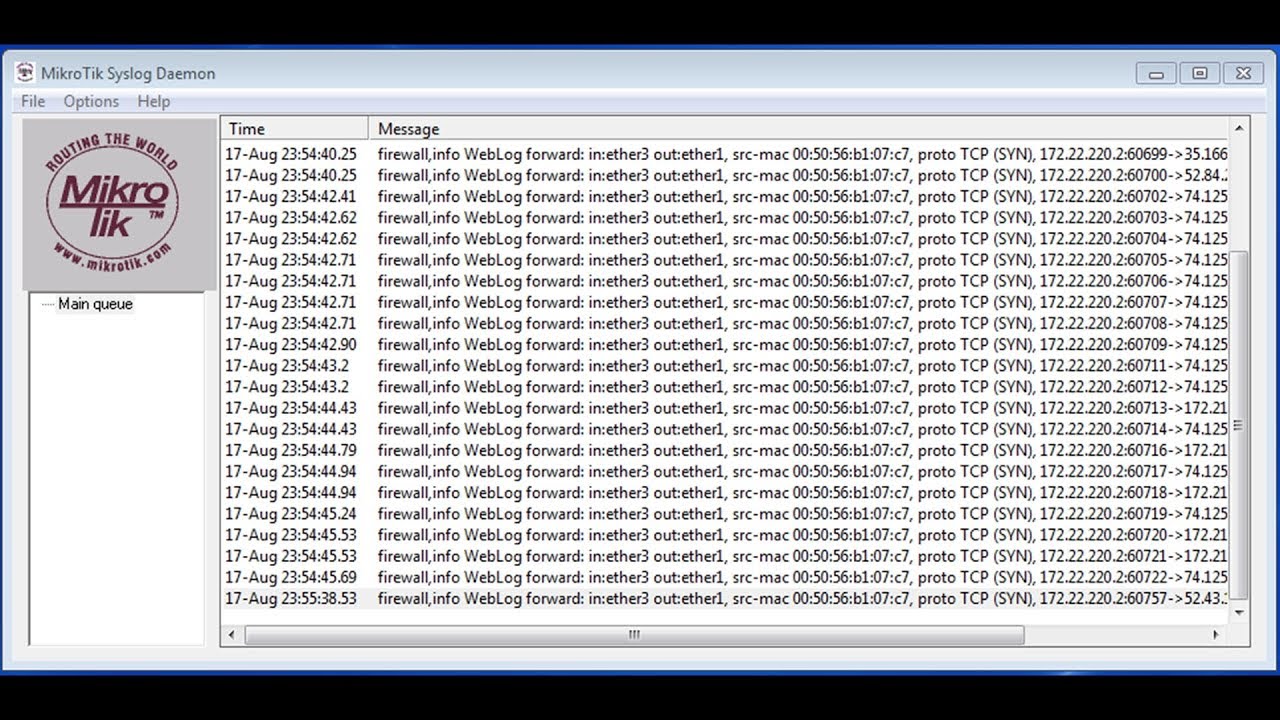




![minipost] Mikrotik/RouterBoard port-knocking example for firewall/NAT openings – NetworkGeekStuff minipost] Mikrotik/RouterBoard port-knocking example for firewall/NAT openings – NetworkGeekStuff](http://networkgeekstuff.com/wp-content/uploads/2014/06/Mikrotik_port_knocking.png)